IMDEA Networks

Event Category: External Presentation (External Speaker)
Blockchain is dead, long live blockchain! Exploiting Accountability to Strengthen Blockchain Fault Tolerance
The long-standing impossibility of reaching an agreement seems to restrict the lifespan of existing blockchains. In fact, consensus is key...
Seguir leyendo arrow_right_altLet’s Work Together: Building a Robust, Consistent, and Efficient Distributed Shared Storage System for Large Data Objects that Promotes Collaboration
A distributed shared storage (DSS) space is a fundamental service to ensure availability, survivability and accessibility to the data that...
Seguir leyendo arrow_right_altIntroduction to FHE, TFHE and Machine Learning Applications
FHE is a technology allowing to perform operations over encrypted data. In this talk, we will do a general introduction...
Seguir leyendo arrow_right_altSGD on Distributed Systems
Deep learning is booming thanks to enormous datasets with very large models, and the widespread availability of supercomputing via GPUs....
Seguir leyendo arrow_right_altOn Three Research Problems
In this talk, I will present applications of the communication theory framework to three research problems. The first is a...
Seguir leyendo arrow_right_altOverview of Adversarial Machine Learning (AML) with Applications to Network Anomaly Detection (NAD)
In this talk, we will give an overview of «adversarial» attacks on deep learning, generally known as adversarial machine learning...
Seguir leyendo arrow_right_altThe hardware and software design for a Cyber-IoT-Physical system
Recently, there has been an enormous interest in Internet of Things (IoT) systems, and a large deployment of IoT systems...
Seguir leyendo arrow_right_altTackling the Energy Asymmetry between Sensing, Computation, and Communication in Wireless Embedded Systems
Wireless Embedded Systems have seen tremendous growth with a vast number of deployed devices, with their numbers continuing to increase...
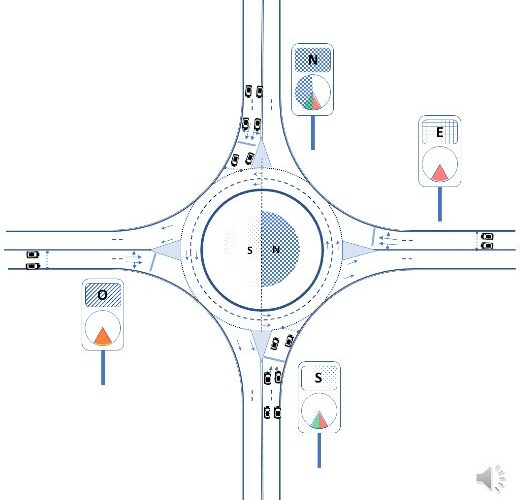
Seguir leyendo arrow_right_altRoundabouts as Switches: Synchro [& Turbo] Roundabouts with Rotating Priority Sectors (STYROPS) for High-Capacity, Safe, and Sustainable Roundabouts
We look at roundabouts as synchronous car multiplexers to overcome the current limitations of roundabouts in capacity, safety, and energy...
Seguir leyendo arrow_right_altHow to Protect Software through Patents and Trade Secrets
Computer programs may be protected by patents if they meet requirements that vary from one jurisdiction to another. We will...
Seguir leyendo arrow_right_alt








Comentarios recientes