IMDEA Networks

Archivos: Events
An Exploration of Cloud Gaming Research in the Era of Edge Computing and AI
In today’s increasingly distributed computational landscape, cloud gaming has emerged as a transformative entertainment model. Cloud gaming refers to any...
Seguir leyendo arrow_right_altA Digital Twin Approach to Quantum Key Distribution Under Eavesdropping
Quantum Key Distribution (QKD) enables secure key exchange by leveraging quantum mechanics to provide theoretically unbreakable security. However, practical deploy...
Seguir leyendo arrow_right_altA Glimpse into Convex Agreement
Achieving agreement among the parties in a distributed system is crucial for maintaining consistent views. This becomes particularly challenging due...
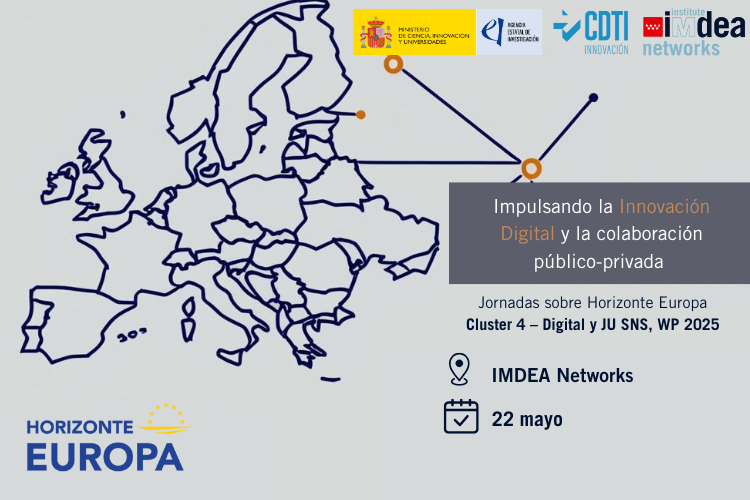
Seguir leyendo arrow_right_altJornadas Cluster 4 HE – Impulsando la innovación digital y la colaboración público-privada
IMDEA Networks, en colaboración con el CDTI, organiza una jornada informativa dedicada a las próximas convocatorias del WP 2025 Clúster...
Seguir leyendo arrow_right_altDUNE: Distributed Inference in the User Plane
Deploying Machine Learning (ML) models in the user plane enables line-rate in-network inference, reducing latency and enhancing scalability for tasks...
Seguir leyendo arrow_right_altDefensa Tesis Doctoral: Data-Driven Exploration of Sociological Patterns in Mobile Network Traffic Demands
This thesis explores the use of mobile network metadata to analyze human sociological behavior and activity patterns. Specifically, it investigates...
Seguir leyendo arrow_right_altA Scalable DNN Training Framework for Traffic Forecasting in Mobile Networks
In this seminar, Serly will present her recent work, accepted in ICMLCN 2025. The exponential growth of mobile data traffic...
Seguir leyendo arrow_right_altAn Evaluation of RAN Sustainability Strategies in Production Networks
In this seminar, Orlando will present his work completed during his research stay at Telefónica, which was accepted at INFOCOM...
Seguir leyendo arrow_right_altFrom Idea to Reality: The Five Pillars of Sustainable Startup Growth
Each year, 50 million new startups emerge worldwide, yet only 10% can sustain themselves in the long run. Cloud computing...
Seguir leyendo arrow_right_altSYMBXRL: Symbolic Explainable Deep Reinforcement Learning for Mobile Networks
Deep Reinforcement Learning (DRL) is a method where an agent, through trial and error, interacts with an environment to gain...
Seguir leyendo arrow_right_alt









Comentarios recientes